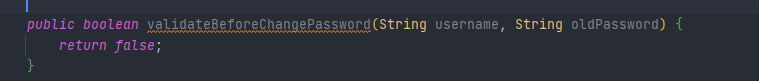
Hi guys,
Assuming I’m logged into an application and have a Keycloak token, now I want to check if the entered password is correct before executing the password.
Please help me write this method in Java, I have tried searching on both Google and ChatGPT but have not found a solution.
I am assuming you are trying to do this using the Admin REST Api.
An option is to initiate a login session with the username and password, and if it’s successful, you can return true, and false if otherwise.
But I have already logged in and have jwt token. So this solution is not feasible.
I don’t think I understood your initial question. what do you mean by “before executing the password”?
are you trying to implement a password change?
Yes, I will have two steps:
- Check if the current password is correct, assuming the user has already logged in.
- If pass step 1, we will update new password
But I am stuck at step 1.
Okay. So my initial answer is feasible. I am aware user is logged in and already has a token, and that does not stop you from initiating another login session.
So here are my (hacky) recommended steps
- Login the user
- User clicks change pass
- ask for old pass
- initiate a login session with username and password in some java method that returns true if the password login session gets initiated successfully.
- update password if true.
- logout the user from all sessions because of password change
An alternative to this would be to just use account reset function which creates a new password without verifying old password but makes use of email verification.
Thanks, I will use your way. ![]()
Hi @adropofliquid
Does this method still works if the user has multi-factor-authentication enabled? If no, then what workaround should we implement in that case?
I have not tried this with MFA enabled. I am not sure about it
Could you please add some code so I can understand.
As I need to build functionality where I have to verify whether the old password is correct or not while changing the password. It would be a great help.
Thanks in advance.
Great work. do you have this on github?
This all is bad in many ways as you build your personal man-in-the-middle ![]()
Better solution:
Leave all to Keycloak, implement your own custom UpdatePassword Required Action by extending the existing/built-in one and overwriting the getMaxAuthAge() method only (or also the order() method) an return 0. Leave the ID of the action as is.
This way, Keycloak will always ask first for the existing password and you don’t have to deal with man-in-the-middle.
Also, don’t do “login” with the man-in-the-middle-apporach. Read and understand the spec and concept behind OAuth2 and OIDC. Don’t argue with “but…”. That’s always wrong.
We are using SSL, how can we meet MITM?
Not to mention, most of the methods that call to Keycloak are doing the same.
Again:
Man-in-the-middle is not about using SSL/TLS or not.
By using you above mentioned approach, your application get access to the users cleartext credentials and thus your application is the MITM! Your application MUST NOT get in touch with users credentials in any ways. Users only interact with the secure server (here: Keycloak) when dealing with credentials.
That’s how OAuth and OIDC work, it’s about redirections in browser, not trying to integrate something in a wrong and highly insecure way into your application.
The Keycloak admin client you are using here is for - guess what - administrational stuff! Not dealing with users credentials and login of users. Just because something works or is possible, doesn’t mean that you are doing it correct. ![]()
Oh, I understood. U mean our system shouldn’t work directly with the user’s credentials request, just working directly with Keycloak, right?
Thank you for your response Niko. This is unclear. How do we implement the custom action? can you explain in more details.
Can you explain this process? Why should I use to override this class?
How does it change the process which has been described here?
As of today, you don’t have to override anything anymore, it’s now a feature in Keycloak that you can define a Password Policy that sets the max. authentication time a user may be authenticated, before asking for reauthentication again. If set to 0, the user will always be asked before updating the password.
The “why” I already explained in my above comment: Validate current password before update new password Keycloak using Spring Boot - #13 by dasniko