I am running keycloak behind an nginx proxy. The nginx proxy is terminating encryption using a self-signed certificate. Both keycloak and the nginx proxy are running as docker containers. My configuration works in dev mode, but in production I get a party blank screen when I try to access the admin console.
Does anyone know what might be causing this? I don’t see any obvious errors in the browser console or networking tab.
Here is an screenshot of my problem:
My docker compose:
keycloak:
container_name: hxd-keycloak
restart: "always"
image: hyperxdashboard-keycloak:latest
environment:
# KC_DB: mariadb
KC_DB_URL_HOST: hxd-mariadb
KC_DB_URL_PORT: 3306
KC_DB_URL_DATABASE: keycloak
KC_DB_USERNAME: ${DASH_DB_USERNAME}
KC_DB_PASSWORD: ${DASH_DB_PASSWORD}
KC_HOSTNAME: "192.168.74.247"
# KC_HOSTNAME_PATH: "https://192.168.74.247:443/auth"
KC_HOSTNAME_PORT: 443
# This is false assuming the proxy handles encryption. Don't expose keycloak to a network unencrypted!
KC_HOSTNAME_STRICT: false
KC_HTTP_ENABLED: true
# KC_HTTP_RELATIVE_PATH: "auth"
KC_HTTP_PORT: 14040
# KC_HTTPS_PORT: 14040
KC_PROXY: "edge"
KEYCLOAK_ADMIN: "${KEYCLOAK_ADMIN_USERNAME}"
KEYCLOAK_ADMIN_PASSWORD: "${KEYCLOAK_ADMIN_PASSWORD}"
ports:
- 14040:14040
depends_on:
- hxd-mariadb
networks:
- hxd-network
My nginx conf:
upstream auth {
server hxd-keycloak:14040;
}
server {
listen *:443 ssl;
listen [::]:443 ssl;
keepalive_timeout 70;
ssl_certificate selfsigned.crt;
ssl_certificate_key private.key;
location /auth {
proxy_buffers 4 256k;
proxy_buffer_size 128k;
proxy_busy_buffers_size 256k;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_pass http://auth$request_uri;
proxy_read_timeout 90;
}
You have many similiar discussion on github.
For example:
opened 06:07PM - 02 May 22 UTC
closed 02:03PM - 14 Jun 22 UTC
kind/bug
area/dist/quarkus
status/triage
### Describe the bug
Following (https://github.com/keycloak/keycloak/issues/108… 17), I've updated keycloak the newest version (18), and I'm still running in to some issues.
As described, the current proxy setting is **edge**
First issues is that when the server is first spawn up, we get a **redirect_uri** error:

LOGS:
> DEBUG [io.quarkus.vertx.http.runtime.ForwardedParser] (executor-thread-11) Recalculated absoluteURI to http://something.com/auth/realms/master/protocol/openid-connect/auth?client_id=security-admin-console&redirect_uri=https%3A%2F%2Fsomething.com%2Fauth%2Fadmin%2Fmaster%2Fconsole%2F&state=fbd3f10a-d929-4af8-a4ce-e3ef06c1b89e&response_mode=fragment&response_type=code&scope=openid&nonce=ea937eae-bcc6-4bf3-aae3-0a4b3742c9d7&code_challenge=pNq3qur9_XOZfrTirOaHRMxCx8pdGL-yeFjAKbLLiHA&code_challenge_method=S256
> DEBUG [org.keycloak.protocol.oidc.utils.RedirectUtils] (executor-thread-11) replacing relative valid redirect with: http://something.com/auth/admin/master/console/*
> WARN [org.keycloak.events] (executor-thread-11) type=LOGIN_ERROR, realmId=a1634d31-f503-4b6b-9ce9-522e84855fc7, clientId=security-admin-console, userId=null, ipAddress=40.41.43.44, error=invalid_redirect_uri, redirect_uri=https://something.com/auth/admin/master/console/
Here we can see that calls are reaching the keycloak server as **http**, so I'm guessing that nginx ingress is forwarding the headers correctly, however its expected that the server knows that its being redirected from an **https** origin and should allow for access as such. This does not happen as we get the aforementioned **redirect_uri** error.
To fix this, we need to add the **absoluteURI** to the redirect_uris of the **security-admin-console** client using kcadm:
> ./kcadm.sh update clients/<ID> -s 'redirectUris=["https://something.com/auth/*"]' --no-config --server http://localhost:8080/auth --realm master --user admin --password admin
We can now enter the password and the user to get access to the admin console, but some requests are generated with the wrong **scheme**:
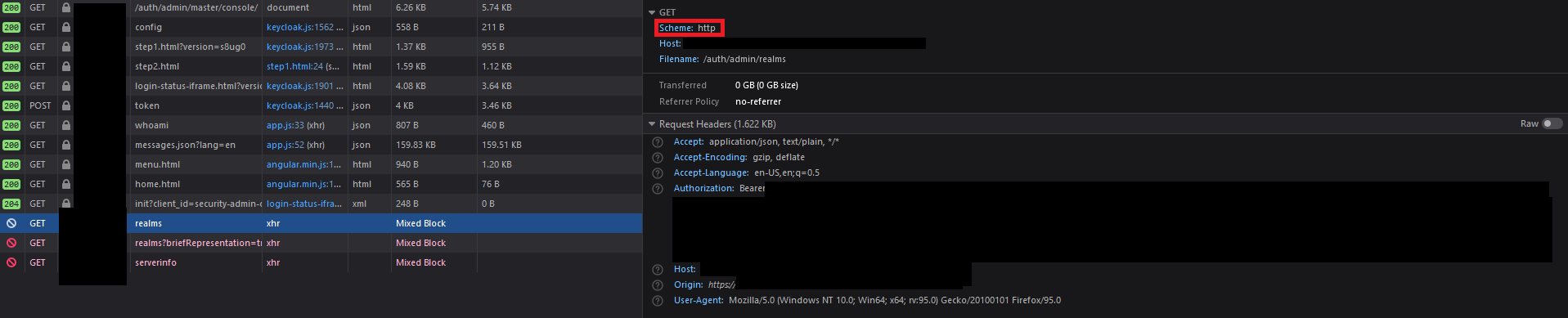
If we copy the request as cURL we get the following:
> curl '**http**://something.com/auth/admin/realms' -H 'User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:95.0) Gecko/20100101 Firefox/95.0' -H 'Accept: application/json, text/plain, */*' -H 'Accept-Language: en-US,en;q=0.5' -H 'Accept-Encoding: gzip, deflate' -H 'Authorization: Bearer <_TOKEN_>' -H 'Origin: https://something.com'
As we can see the address is generated with **HTTP**, at this point the browser identifies this as a possible risk and flags the requests as **MIXED BLOCK**. I'm not able to get any logs from this as the browser doesn't even try to reach the server. However if we take this and change to **HTTPS** and run the cURL command its is successful.
There are however some requests that are generated correctly:
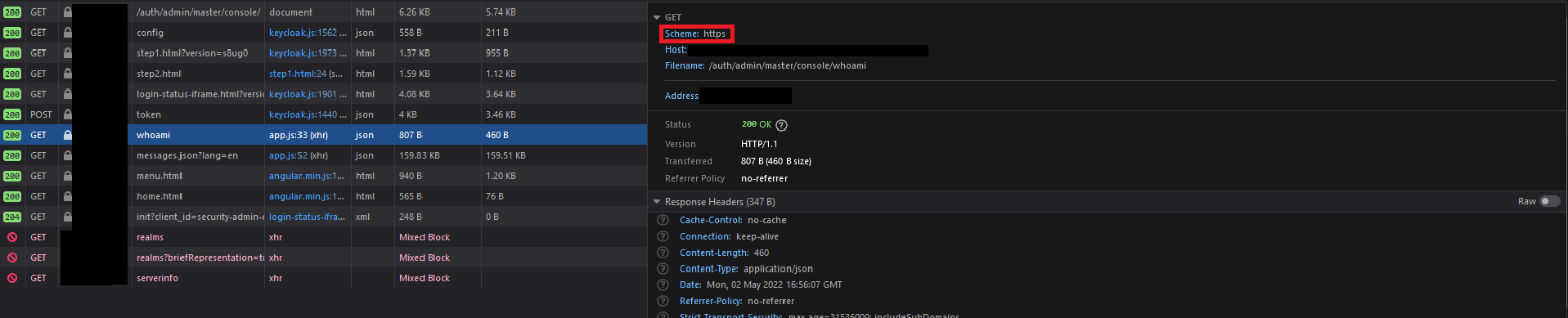
So my guess is that something in the client-sided application is generating the urls incorrectly.
Is this a known bug or is it some miss configuration on my side?
My current setup is as follows:
KEYCLOAK 18 (quarkus):
KC_PROXY=EDGE
KC_HOSTNAME=something.com
KC_PORT = 8080
KC_HTTP_RELATIVE_PATH=/auth
Cloud Provicer is AWS
Running on Kubernentes (EKS)
INGRESS-CONTROLLER = nginx
Ingress variables:
host: something.com
path: /
port: 8080
### Version
18
### Expected behavior
Not getting redirect_url error and being able to access the admin console.
### Actual behavior
Getting redirect_url on a fresh instance and not being able to access the admin console.
### How to Reproduce?
Spawn a new keycloak instance in kubernetes with **KC_PROXY=edge** and with an nginx ingress. Then just access the browser on the defined url.
### Anything else?
https://github.com/keycloak/keycloak/issues/10817
https://github.com/keycloak/keycloak/issues/11667
https://keycloak.discourse.group/t/mixed-block-error-on-api-request-on-the-admin-console/15178
Maybe that can help you. What i see is that you commented out relative path but your nginx config redirects to auth.
One other thing is you havent set the
I think you see partly the admin page because of the browsers cache.
1 Like
Thanks for your reply Paul! I looked through the GitHub and I found this bug report that seemed similar to my issue. After removing “KC_HOSTNAME_PORT: 443” from my docker compose, everything works!
In case you’re curious, I commented out the KC_HTTP_RELATIVE_PATH line in my compose because I’m setting that variable at build time in my DockerFile. Production mode seems to want you to get that variable at build time, while dev mode wants you to set it at runtime. Kinda strange behavior.
I also tried clearing my cache, but that top section of the admin page was still visible. In any case, removing KC_HOSTNAME_PORT seems to have fixed my issue!
2 Likes
thanks Peter-CA for posting this…I’d read docs and blogs and tried various env var combos and configs but was still stuck with a completely blank admin console page. removing KC_HOSTNAME_PORT as per your followup post fixed it for me… much appreciated! Need to upskill on keycloak for sure!
2 Likes
Thank you so much! Removing KC_HOSTNAME_PORT worked for me. It’s curious that for dev mode, it only work with KC_HOSTNAME_PORT.
